Multi-Factor Authentication Overview
As part of the College’s response to the threat posed by cybercriminals, and regulatory requirements, login access to mySCC and Moodle will be integrated with Multi-Factor Authentication (MFA) starting Tuesday, January, 3, 2023.
Our implementation of MFA will allow for one of the following methods of authenticating after you enter your username and password:
- Cell phone to receive a text or access the Authenticator App
- Telephone number to receive a call
- An electronic card that will generate a code
Students and Employees who do not have access to an alternate email, cell phone, or telephone number will require an electronic card. To obtain a card, fill out the "MFA Token Request” for approval. Allow at least one week to process your request. The cards will be pre-programmed and can be picked up at IT helpdesk with proper ID.

How To Set up Multi-Factor Authentication for SCC Accounts
We have included a video tutorial that details how to use Microsoft Authenticator for the MFA process. Alternatively, we have created a step-by-step instruction guide to help you complete this process. We recommend that you utilize the Microsoft Authenticator app, which is available in the app stores for both iOS and Android devices. Completing the one-time setup with the app greatly simplifies the process going forward.
Step-By-Step Instructions
To set up MFA for your account, you can either use the Microsoft Authenticator App or receive a code sent to your phone. Below are step-by-step instructions for both.
IMPORTANT: Your MFA will last for 24 hours unless you change to a different device (different computer or phone) or physical location such as home (a different network) for your login. At that point it will force you to authenticate again every instance
Configure your Microsoft account
- Go to https://aka.ms/mfasetup and login using your MySCC credentials
- Once logged in, go to Security Info
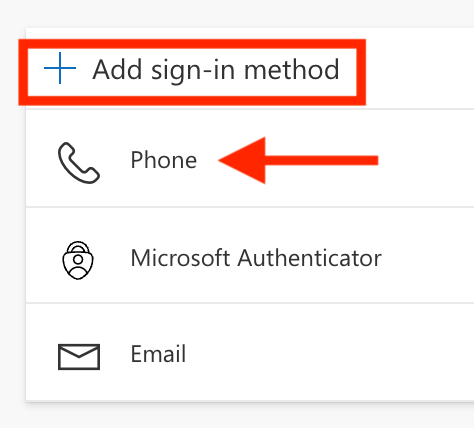
- Click Add sign-in method link
- Next you must choose to add methods by which you can be authenticated. Here are the preferred methods from weakest to strongest for MFA:
- Text Message (SMS) or Email: When you login to an account, the service will send a code to your phone or email account, which you then use to login. Note that this SMS/mail is the weakest form of MFA, and you should only use it if none of the other options are available.
- Authenticator App: An authenticator app is one that generates MFA login codes on your smartphone or token device. When prompted for your MFA code, you launch the app or look at your token device and type in the displayed number. These codes often expire every 30 or 60 seconds.
- Push Notification: Instead of using a numeric code, the service “pushes” a request to your phone to ask if it should let you in. You will see a pop-up and can approve the login request or deny it if you did not initiate the authentication request.
- FIDO authentication: FIDO stands for "Fast Identity Online" and is the gold standard of multi-factor authentication. The FIDO protocol is built into all major browsers and phones. It can use secure biometric authentication mechanisms – like facial recognition, a fingerprint, or voice recognition – and is built on a foundation of strong cryptography. Often it uses a physical device – a key – essentially an encrypted version of a key to your house.
SMS - Option 1
Choose Phone and click Add. You’ll be prompted to enter your mobile # and be sent a text with a code to enter and validate.
Authenticator - Option 2 (HIGHLY RECOMMENDED)
Choose the Authenticator App and click Add. You’ll be prompted to get the Authenticator App for your mobile device. Go to Step 5 on your mobile device then you’ll come back to your computer for Step 6.
Go to https://www.microsoft.com/en-us/security/mobile-authenticator-app on your mobile device or use the QR code below to install the Microsoft Authenticaor App:
NOTE: Make sure you download the app that says Microsoft Authenticatior which should NOT cost you anything.


Once the mobile app is installed on your mobile device, on your computer go back to where you left off on Step 4 and click Next
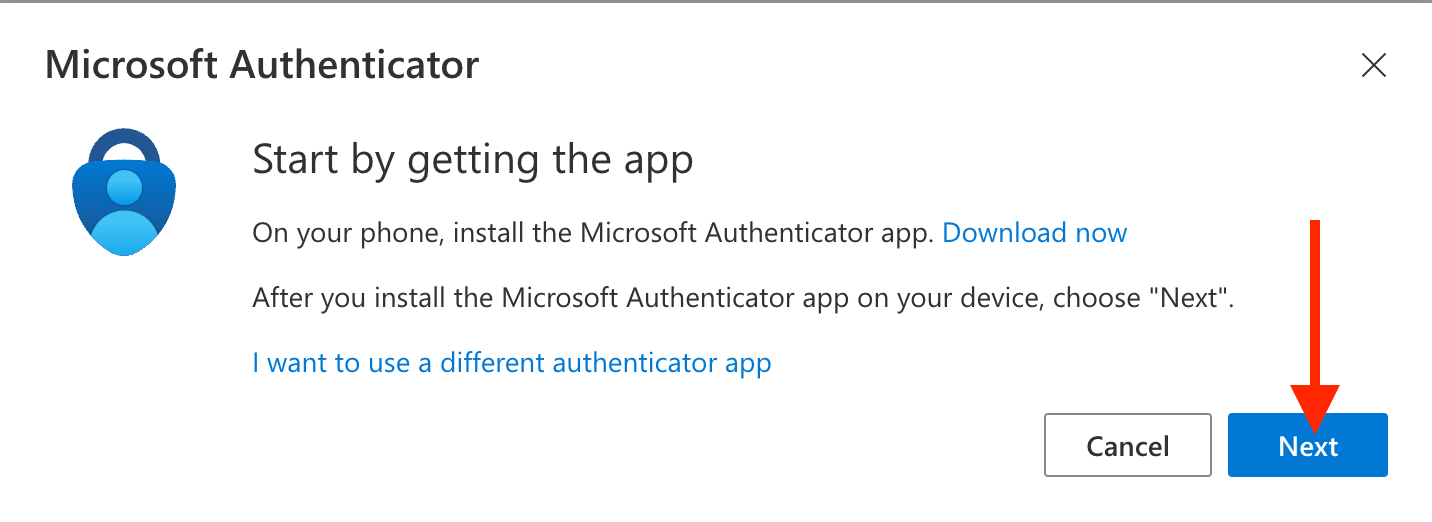
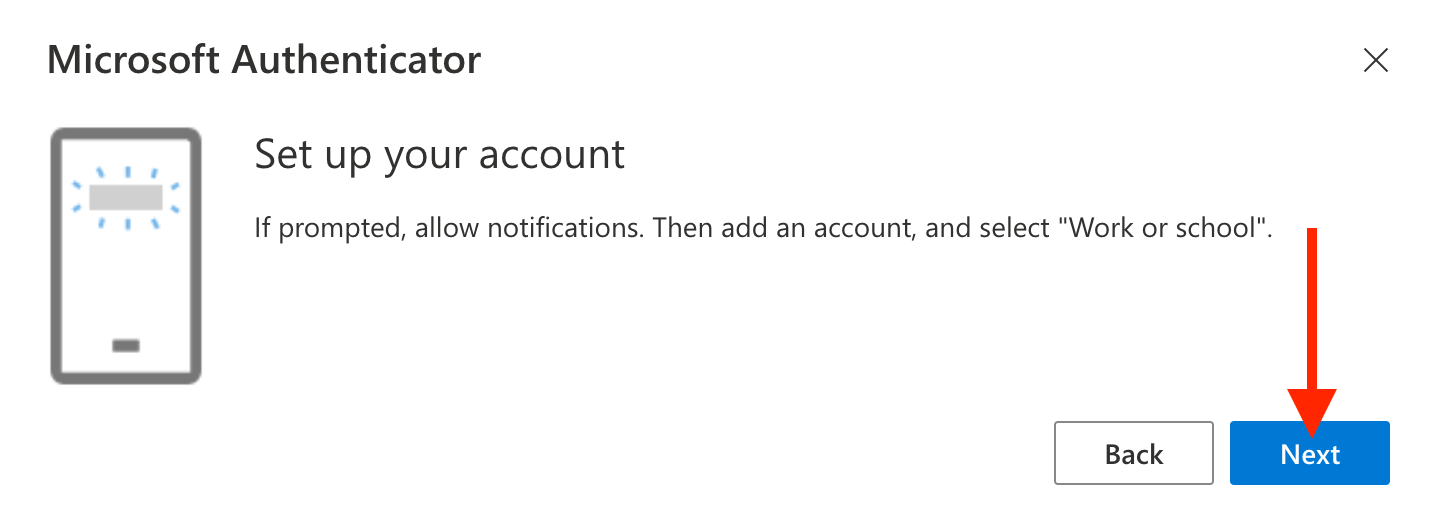
Click Next and prepare to use a QR code on your mobile device to authenticate through the Authenticator app
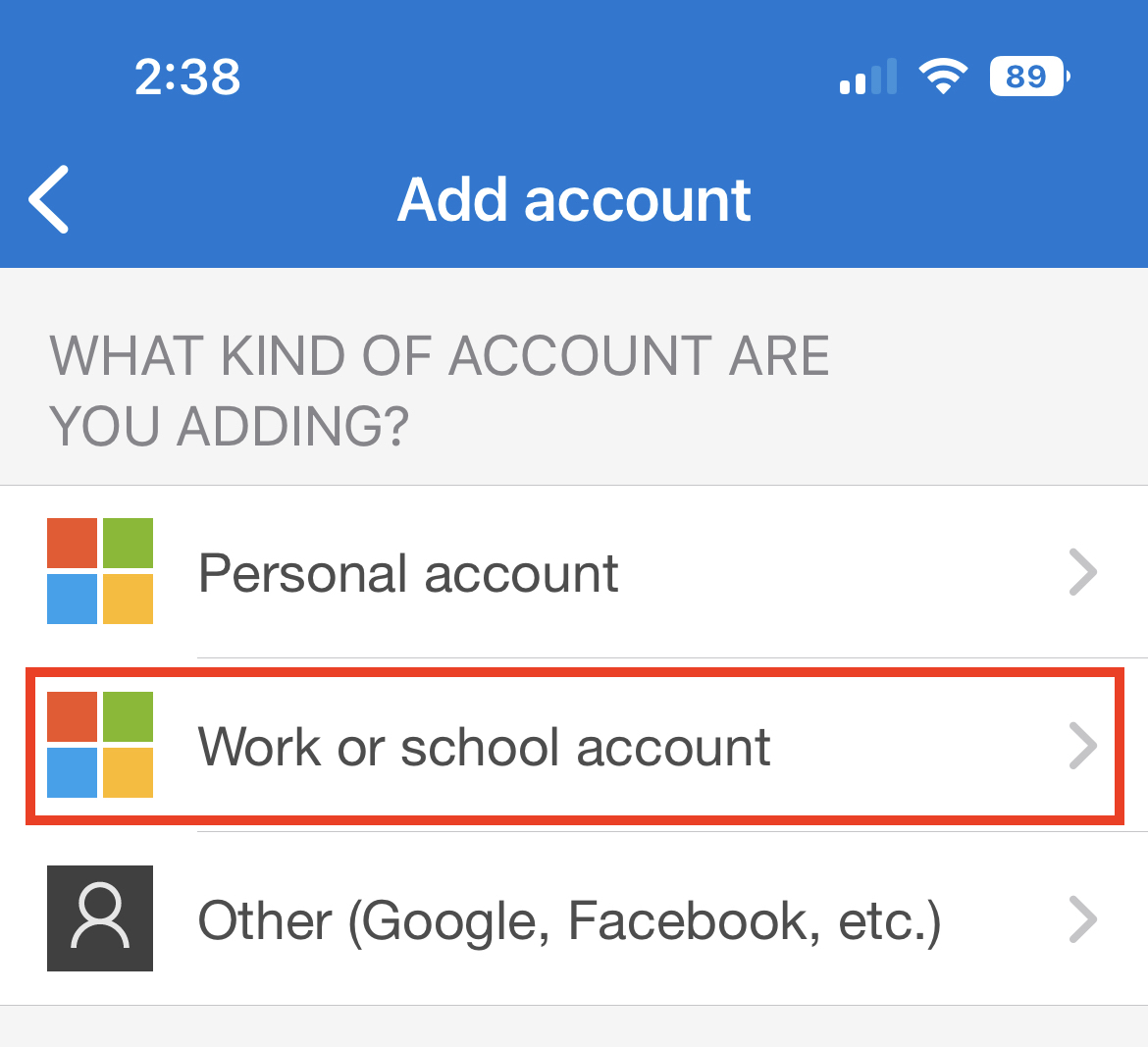
On your mobile device, in the Authenticator app, click the “+” on the top-right corner to add an account. Choose Work or School Account as the type

Tap Scan QR Code
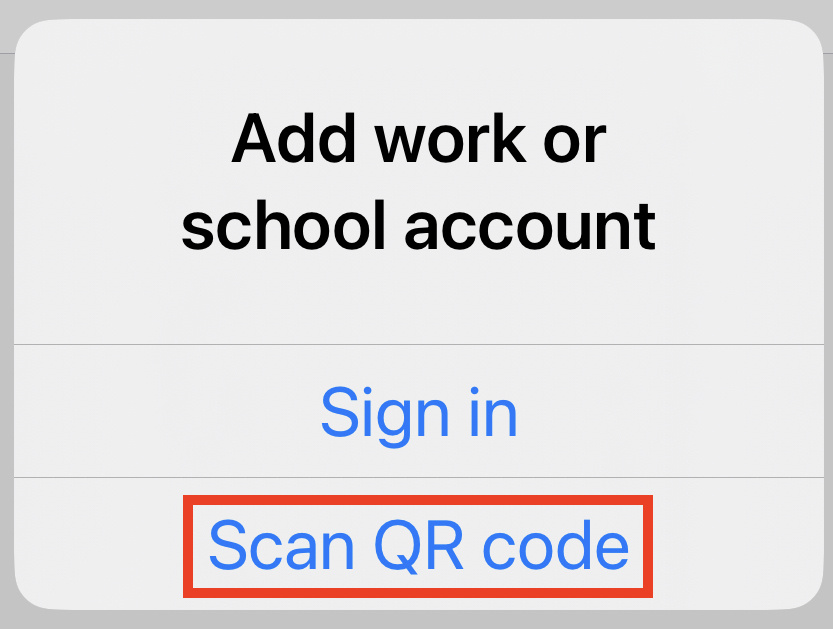
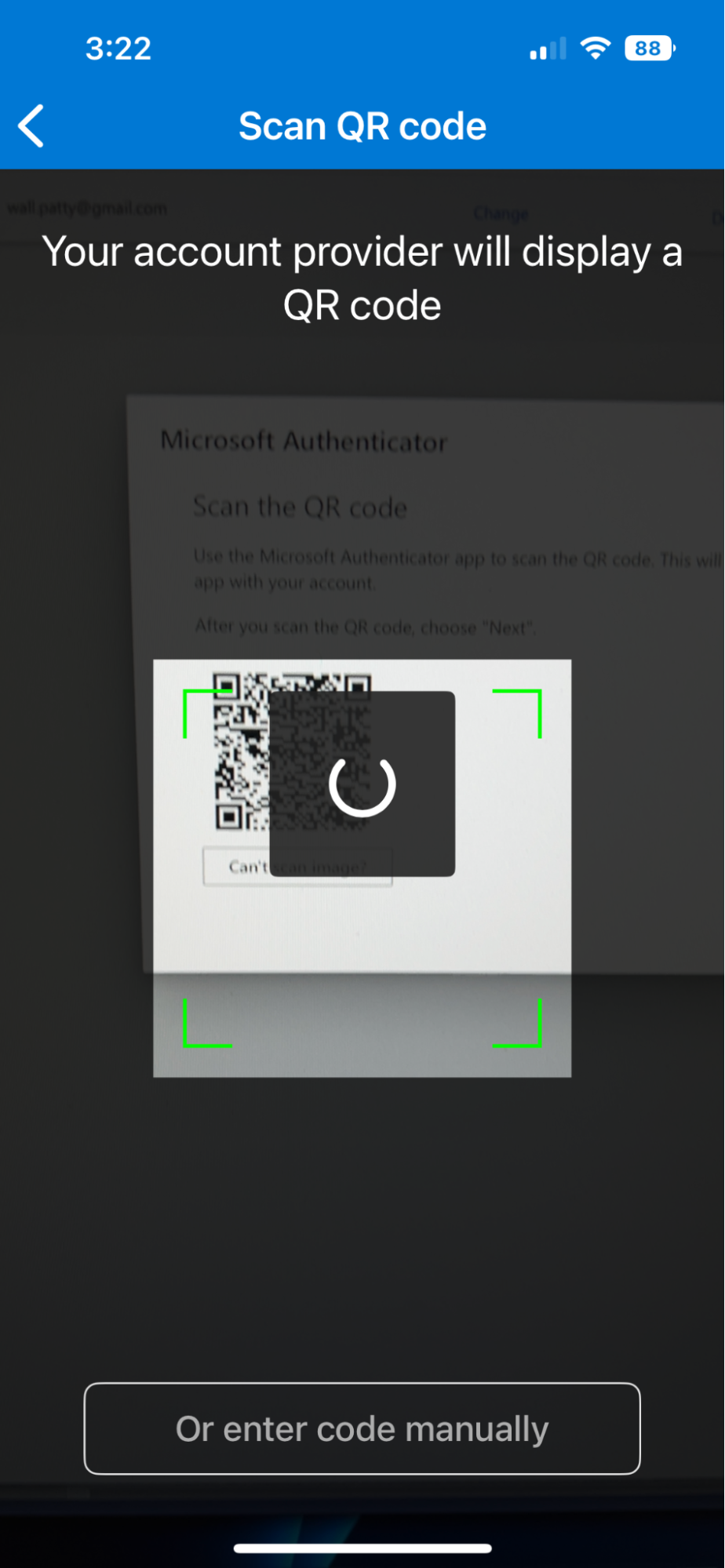
In the Authenticator app, hold your phone camera in front of the QR code on your computer screen and scan the QR code
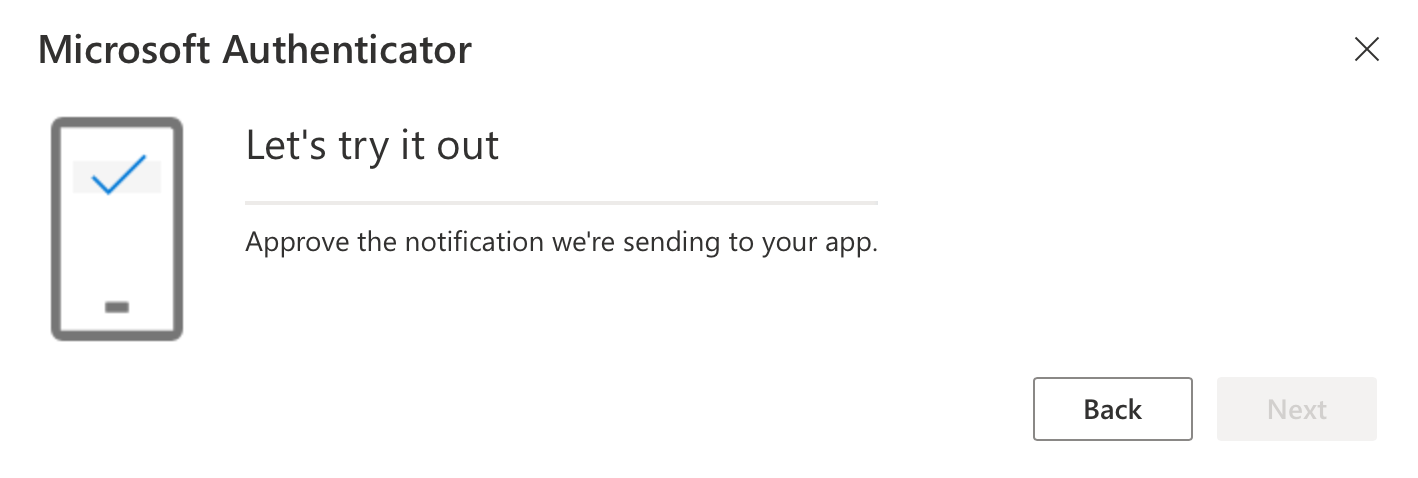
Next, do the initial authentication test on your mobile device and click Next

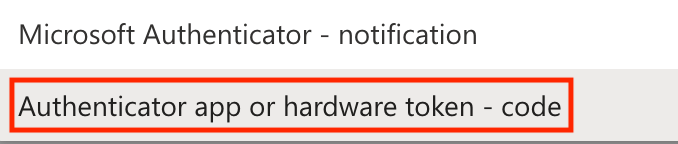
- Next, on the web site login for Microsoft, you are highly recommended to change the default sign-in method to be Authenticator app or hardware token.
- Change it to be Authenticator App or Hardware Token - Code
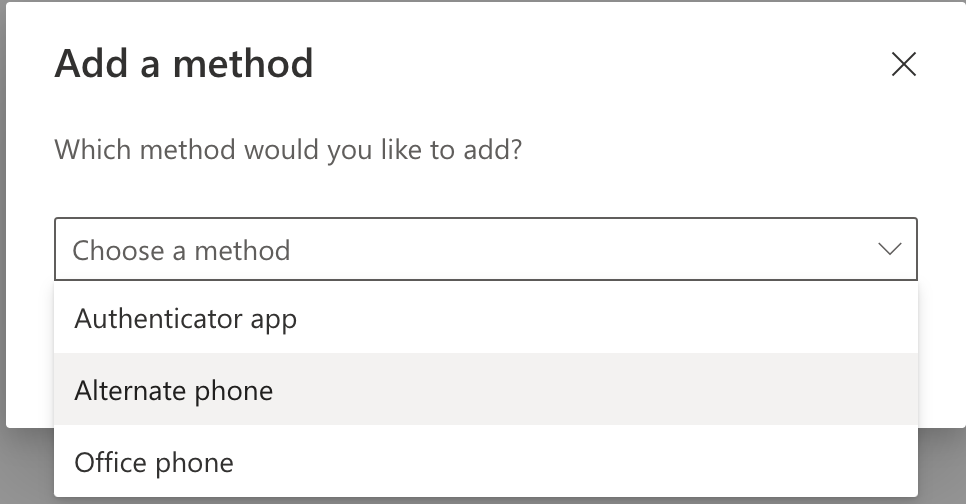
- Optional: Add alternate/backup methods if you choose
- You can exit the Microsoft account page
- The next time you login to an SCC-managed information system and are asked to verify with Microsoft, which will look like the image below, you will be required to use one of the MFA methods you set up above.

- IMPORTANT: Your MFA will last for 24 hours unless you change to a different device (different computer or phone) or physical location such as home (a different network) for your login. At that point it will force you to authenticate again every instance.

